✨ Now Available! Download Lokker’s March 2024 Online Data Privacy Report “Quantifying Web Privacy Risks.“
Real-time data protection for
the web.
Eliminate privacy threats without
affecting
web functionality.
Privacy Edge® Provides Real-Time Protection from Web Privacy Threats.
privacy laws.
Scan and confirm if your privacy program and consent management are working correctly.
Eliminate your exposure to unauthorized scripts with real-time blocking technology.
Protect your customers’ data in real time with website data loss prevention (DLP).
Customize your data compliance based on jurisdictional requirements.
Explore how privacy edge works


Cookie Consent is Not Enough.
Privacy regulations like the CPRA, HIPAA, and GDPR require explicit permission from visitors to collect and share their data.
Protect your visitors by allowing customers to opt into safe, vetted trackers and cookies that won’t put their privacy at risk and will keep your company compliant. Privacy Edge works alongside your consent tools by providing continuous, real-time detection, alerting, and blocking of trackers and cookies in every web session.
Explore how privacy edge works
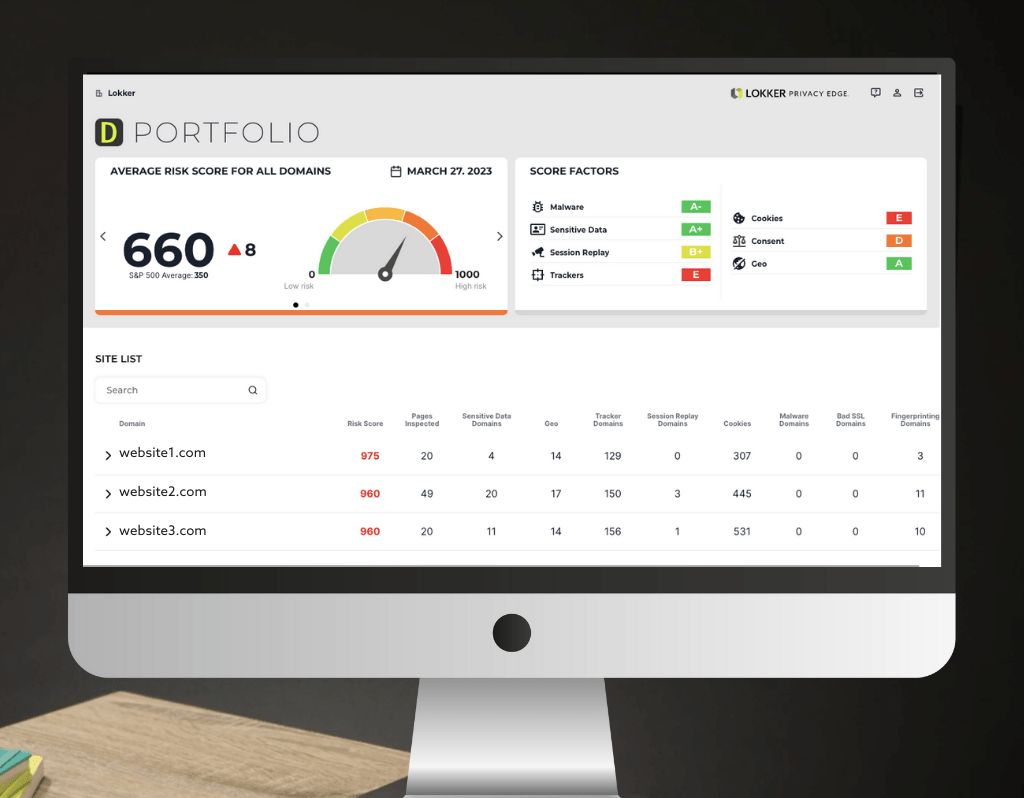
Know Your Risk.
Learn More About The LOKKER Web Privacy Risk Score™
Lokker In The News

Catch LOKKER CEO Ian Cohen on the “What The Hack” Podcast
Tune in as Ian talks with the hosts about the technological challenges of companies really protecting their customers’ privacy, not to mention the new (and

Interview of LOKKER CEO, Ian Cohen, Featured in Insurance Business America article “How well do your clients know their data privacy risks?”
LOKKER CEO Ian Cohen explains how class-action suits and regulatory measures are putting more pressure on organizations to protect their customers’ privacy on public-facing company

LOKKER research featured in “Consumer Data Bonanza Over Cyber Weekend”
Research and insights from LOKKER’s 2022 Holiday Shopping Data Privacy Report were the basis for the article in Multichannel Merchant. The report looked at the

LOKKER mentioned in “Clinic Reports Tracking Pixel Breach Involving 3rd Party”
BayCare Clinic in Wisconsin reported a data breach to the U.S. Department of Health and Human services as a result of patient data being exposed